Imagine this: a critical machine fails, halting your entire production line. But what if the culprit wasn't a random breakdown, but a hacker lurking in your network?
The Internet of Things (IoT) is revolutionizing manufacturing, but with increased connectivity comes new security risks. Here's how to fortify your industrial IoT (IIoT) defenses!
Introduction
The increasing connectivity in the manufacturing sector, driven by the Internet of Things (IoT), brings along new security challenges. In this article, we'll explore five essential tips to secure your Industrial IoT (IIoT) network, ensuring the safety and efficiency of your operations.
Now, let's dive deeper into each of these crucial strategies:
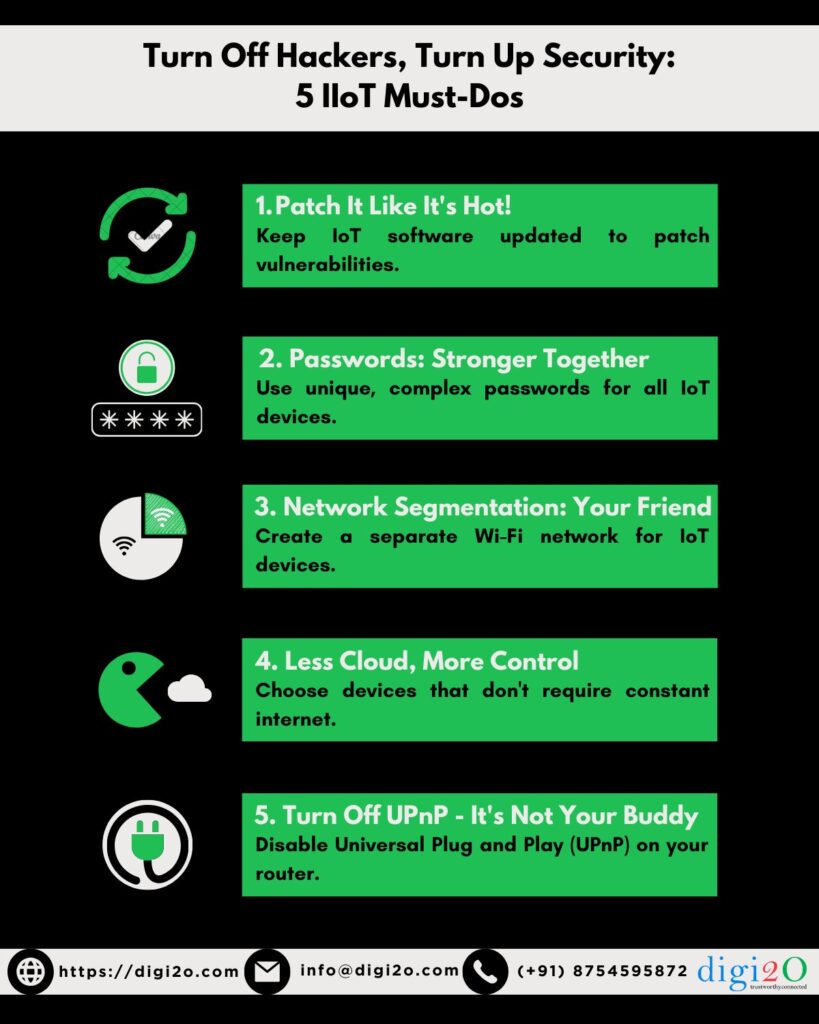
Just like your phone, IoT devices need software updates to fix vulnerabilities. Don't be complacent - install them ASAP! This might not be as automated as your PC, so stay vigilant.
Software vulnerabilities are like open doors for hackers. Just as you update your computer and phone regularly, ensure your IoT devices receive timely patches. Keep an eye on updates and apply them promptly to keep your network fortified against potential threats.
Ditch the factory default passwords! Create unique, complex passwords for every device and account. Think numbers, letters, and symbols - the more random, the better. Pro tip: Don't reuse passwords across different devices!
Default passwords are the low-hanging fruit for cyber attackers. Set strong, unique passwords for each device and account to create layers of defense. Use a combination of letters, numbers, and symbols to make them resilient against brute force attacks.
Think of your network as a fortress with multiple layers of defense. By segmenting your network and creating dedicated zones for IoT devices, you limit the impact of a breach. Even if one area is compromised, the rest of your network remains secure.
Imagine creating a separate Wi-Fi network just for your IoT devices. This way, even if a hacker breaches your IIoT network, they'll have a harder time reaching your critical systems.
While cloud services offer convenience, they also introduce vulnerabilities. Consider local solutions that reduce dependence on the cloud, minimizing the exposure of sensitive data to potential breaches. This approach puts you in control of your data and security measures.
Universal Plug and Play (UPnP) might simplify device connection, but it also creates security holes. Unless necessary, disable this feature to make life harder for potential attackers. UPnP may seem convenient, but it's a double-edged sword when it comes to security. Disabling UPnP reduces the attack surface by closing unnecessary ports and thwarting potential intruders. Take control of your network by disabling this feature unless absolutely necessary.
Conclusion
Securing your IIoT network is paramount in today's interconnected world. By implementing these five essential tips, you can bolster your defenses against cyber threats, safeguarding your operations and ensuring uninterrupted productivity.
By following these steps, you can significantly reduce your IIoT security risks. Remember, a proactive approach is essential to safeguard your factory from cyber threats!
Designed by W3Squad