
Thinking about bringing your designs to life with 3D printing? It's an exciting journey into a world where imagination meets technology. But amidst the vast array of options available, selecting the ideal additive manufacturing (AM) technology can feel like navigating a maze. Fear not! This guide is here to illuminate your path.
Before diving into the realm of 3D printing, you'll need a digital blueprint of your creation. This is where Computer-Aided Design (CAD) software comes into play. Whether you're crafting custom prosthetics, architectural wonders, or intricate automotive parts, your design is the cornerstone of the entire process.
Just like a chef prepares ingredients before cooking, your 3D printer requires some pre-printing groundwork. This involves slicing your 3D model into thin layers, adjusting printing parameters such as resolution and infill density, and ensuring your machine is primed for optimal performance.
With your design finalized and your printer primed, it's time to witness the magic of additive manufacturing in action. Layer by layer, your chosen 3D printer will bring your digital creation into the physical realm, transforming mere data into tangible objects with remarkable precision.
While some 3D prints emerge from the printer in pristine condition, others may require a bit of post-processing finesse. This could involve removing support structures, sanding rough edges, applying surface treatments for a polished finish, or even painting to add a personal touch.
Now, let's delve into the crucial task of selecting the right AM technology for your specific needs. Several factors will influence your decision, including:
By meticulously considering these factors, you'll be equipped to make informed decisions that align with your project requirements and unlock the full potential of 3D printing technology.
Embarking on a 3D printing journey is a thrilling endeavor, fueled by innovation and boundless creativity. By following this step-by-step guide and integrating key considerations into your decision-making process, you'll embark on a path paved with endless possibilities. Whether you're a seasoned engineer, a budding entrepreneur, or an avid hobbyist, the right additive manufacturing technology awaits, ready to transform your visions into reality. So, dare to dream, design with purpose, and let the magic of 3D printing propel you toward a future limited only by your imagination.

In today's fast-paced industrial landscape, the integration of technology has revolutionized manufacturing processes. One such advancement is the adoption of Industrial Internet of Things (IIoT), which enables real-time monitoring, data analysis, and automation of industrial systems. However, with these benefits come significant security challenges. The interconnected nature of IIoT devices creates vulnerabilities that can be exploited by malicious actors. In this comprehensive guide, we will explore step-by-step strategies to build a secure IIoT network and protect your operations from cyber threats.
The rise of Industrial IoT (IIoT) presents immense opportunities for streamlining processes and optimizing performance. Yet, it also exposes your operations to unprecedented cybersecurity threats. To safeguard your smart factory from potential breaches and ensure uninterrupted production, it's imperative to fortify your IIoT network.
Segmentation:
Segmenting your network is akin to compartmentalizing your fortress. By isolating devices into distinct zones, you mitigate the risk of a single breach compromising your entire system.
Fortress Firewalls:
Deploy robust firewalls as vigilant sentinels guarding your digital perimeter. These firewalls regulate traffic flow, permitting only authorized communication while thwarting malicious intrusions.
Encrypted Communication Channels:
Employ encryption protocols to cloak your data in impenetrable layers. Encrypting communication channels renders intercepted data indecipherable, safeguarding sensitive information from prying eyes.
Strong Authentication:
Equip your devices with formidable digital defenses - strong, unique passwords and multifactor authentication. These authentication measures act as digital padlocks, fortifying access points against unauthorized entry.
Regular Software Updates:
Stay ahead of potential vulnerabilities by diligently applying software patches and updates. Updating your devices is akin to fortifying your defenses, ensuring they remain impervious to evolving cyber threats.
Feature Management:
Mitigate risk by disabling unnecessary features and functionalities on your devices. By minimizing the attack surface, you reduce the likelihood of exploitation by cyber adversaries.
Continuous Monitoring:
Maintain unwavering vigilance over your IIoT network with round-the-clock monitoring. Like a vigilant guard, remain alert for any signs of suspicious activity, swiftly identifying and neutralizing potential threats.
Isolation Plan:
Prepare a comprehensive strategy to isolate and quarantine compromised devices in the event of a breach. Swift containment prevents the escalation of threats, minimizing the impact on your operations.
Incident Recovery Plan:
Develop a robust incident recovery plan to swiftly bounce back from cyberattacks. A well-defined recovery strategy minimizes downtime and financial losses, ensuring business continuity in the face of adversity.
In conclusion, securing your Industrial IoT network is not merely a choice; it's a necessity in today's digital landscape. By implementing the aforementioned measures, you fortify your smart factory against cyber threats, safeguarding your operations and preserving your competitive edge.
Let's continue the dialogue! Share your insights and experiences regarding IIoT security in the comments below.
"The greatest glory in living lies not in never falling, but in rising every time we fall." - Nelson Mandela
Just as Nelson Mandela epitomized resilience, your IIoT network must embody the same spirit. Proactively adopt these security measures to pave the way for a secure and prosperous industrial revolution within your factory!
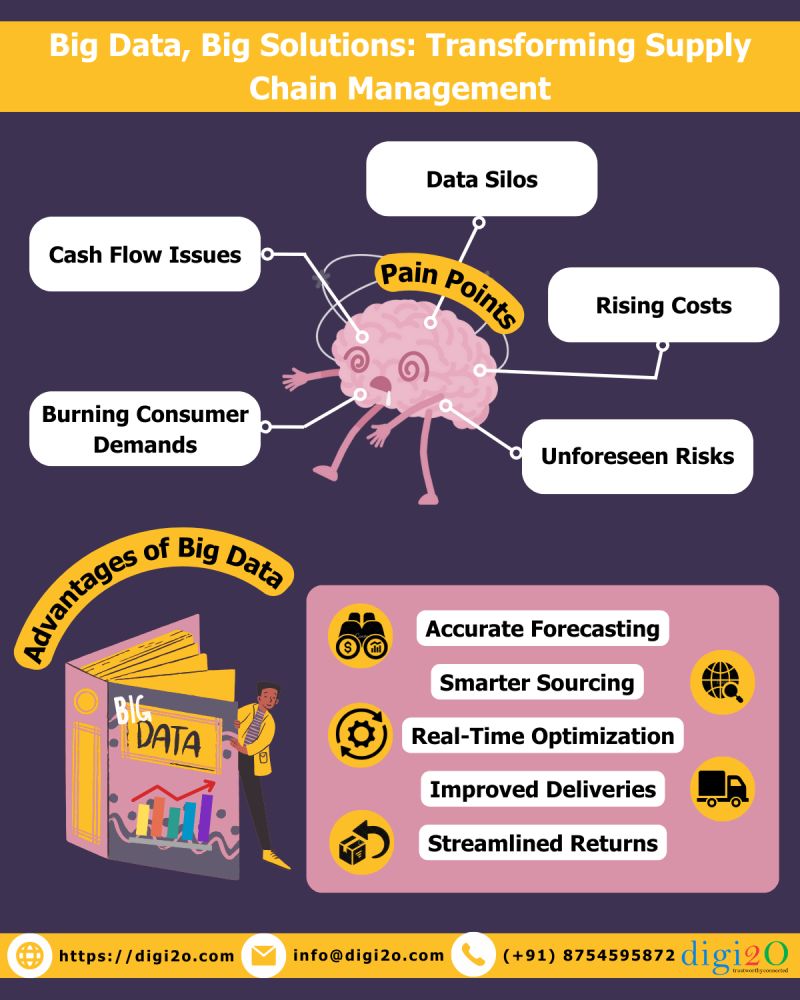
In today's dynamic business landscape, where the global market is more interconnected than ever before, supply chain efficiency stands as a cornerstone of success for enterprises across industries. The ability to streamline operations, optimize resources, and meet consumer demands promptly is vital for sustainable growth and competitiveness. Leveraging big data emerges as a game-changer in this realm, offering unparalleled insights and opportunities for enhancing supply chain efficiency.
Big data refers to vast volumes of structured and unstructured data generated at an unprecedented velocity. These datasets encompass a myriad of sources, including customer transactions, social media interactions, sensor data, and more. The essence of big data lies in its three defining characteristics: volume, velocity, and variety.
In the context of supply chain management, big data serves as a catalyst for transformative change. By harnessing advanced analytics and machine learning algorithms, organizations can extract valuable insights from vast data sets, enabling data-driven decision-making at every stage of the supply chain.
Big data empowers organizations to predict demand patterns with unprecedented accuracy. By analyzing historical data, market trends, and consumer behavior, businesses can anticipate fluctuations in demand, enabling proactive inventory management and resource allocation.
Efficient inventory management is critical for minimizing costs and maximizing profitability. Big data analytics enable real-time visibility into inventory levels, demand forecasts, and supplier performance, facilitating optimal inventory replenishment and reducing stockouts or excess inventory.
Big data analytics drive operational excellence by identifying bottlenecks, inefficiencies, and areas for improvement within the supply chain. By optimizing route planning, warehouse operations, and transportation logistics, organizations can streamline processes, reduce lead times, and enhance overall efficiency.
Effective collaboration with suppliers is essential for ensuring a seamless flow of goods across the supply chain. Big data facilitates transparent communication, performance tracking, and risk management, fostering stronger partnerships and enabling collaborative problem-solving.
In today's volatile business environment, mitigating supply chain risks is paramount. Big data analytics enable proactive risk identification and mitigation strategies by monitoring factors such as geopolitical events, natural disasters, and supplier disruptions, thereby safeguarding operations and enhancing resilience.
To leverage big data effectively, organizations must centralize and integrate data from disparate sources, including enterprise systems, IoT devices, and external data streams. Implementing robust data governance frameworks and data management solutions is essential to ensure data quality, integrity, and accessibility.
Deploying advanced analytics tools and predictive modelling techniques is crucial for extracting actionable insights from big data. Machine learning algorithms, data visualization tools, and statistical techniques enable organisations to identify patterns, trends, and anomalies, empowering data-driven decision-making and strategic planning.
Building collaborative partnerships with technology vendors, data scientists, and industry experts is instrumental in driving successful big data initiatives. Additionally, investing in talent development and data literacy programs equips employees with the necessary skills and knowledge to harness the full potential of big data analytics.
In conclusion, leveraging big data presents unparalleled opportunities for enhancing supply chain efficiency, agility, and competitiveness. By harnessing advanced analytics, organizations can unlock valuable insights, optimize processes, and mitigate risks, thereby driving sustainable growth and value creation in today's digital era.
Imagine this: a crucial machine breaks down, halting your entire production line. Sound familiar
What if AI could predict these meltdowns and prevent them altogether?
According to a recent TechTarget feature, manufacturers are leveraging AI in powerful ways to boost efficiency, reduce costs, and stay ahead of the curve. Here are 5 examples you can implement today ⭐:
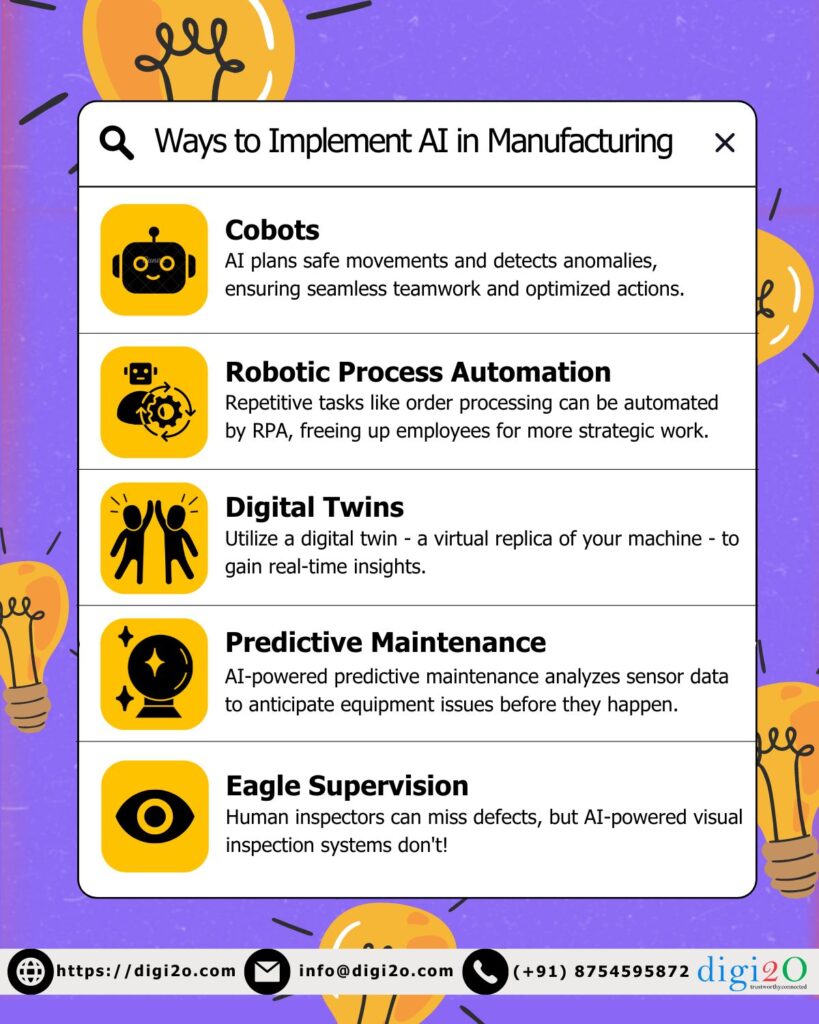
Cobots: Your AI-Powered Teammate
Empower your assembly line with intelligent cobots! These collaborative robots leverage AI for object recognition, adapting to various parts. AI also plans safe movements and detects anomalies, ensuring seamless teamwork and optimized actions. This frees up your team for more complex tasks, while guaranteeing reliable cobot assistance.
RPA Takes Over Tedious Tasks with AI's Help
Repetitive tasks like order processing can be automated by RPA, freeing up employees for more strategic work. AI enhances this by enabling bots to learn and improve accuracy, handle exceptions, and even process unstructured data like emails. This powerful combination maximizes efficiency and lets your team focus on higher-value tasks.
Digital Twins: Know Your Machines Inside Out with AI
Utilize a digital twin - a virtual replica of your machine - to gain real-time insights. AI analyzes sensor data from both, predicting potential failures and optimizing performance. This continuous learning loop ensures proactive maintenance, maximizing equipment lifespan and operational efficiency. Imagine a real-time health check for your machines, fueled by AI's predictive power.
Predictive Maintenance: See the Future (of Your Machines)
Never be caught off guard by a machine failure again! AI-powered predictive maintenance analyzes sensor data to anticipate equipment issues before they happen. This allows you to schedule maintenance proactively, avoiding downtime and saving money.
AI Inspects with Eagle Eyes
Human inspectors can miss defects, but AI-powered visual inspection systems don't! These systems use machine vision cameras to detect flaws in products with incredible accuracy. This ensures you deliver only the highest quality products to your customers.
Ready to revolutionize your factory floor? This is just the tip of the AI iceberg! ✨
The integration of Artificial Intelligence (AI) into manufacturing processes has brought about a significant transformation in the industry landscape. AI technologies offer unparalleled opportunities to enhance efficiency, quality control, and predictive maintenance in manufacturing operations. By harnessing the power of AI, manufacturers can streamline processes, reduce costs, and stay competitive in an ever-evolving market.
In the realm of manufacturing, cobots - collaborative robots powered by AI - are revolutionizing assembly lines. These intelligent machines work alongside human operators, performing tasks that require precision and dexterity. By leveraging AI for object recognition and safe movement planning, cobots ensure seamless collaboration with human workers. This not only boosts productivity but also enhances safety in the workplace.
Robotic Process Automation (RPA) combined with AI is automating repetitive tasks that were once time-consuming for human workers. From order processing to data entry, RPA systems equipped with AI capabilities can handle a myriad of tasks with speed and accuracy. This automation liberates human resources, allowing them to focus on strategic initiatives that drive innovation and business growth.
Digital twins, virtual replicas of physical machines, offer manufacturers invaluable insights into their operations. By integrating AI algorithms, these digital counterparts can analyze real-time sensor data to predict potential failures and optimize performance. This proactive approach to maintenance not only minimizes downtime but also extends the lifespan of equipment, ultimately enhancing operational efficiency.
Predictive maintenance powered by AI is transforming the way manufacturers approach equipment upkeep. By analyzing sensor data and machine learning algorithms, AI can anticipate potential issues before they occur. This foresight enables proactive maintenance scheduling, reducing unplanned downtime and saving costs associated with emergency repairs. Manufacturers can now keep their production lines running smoothly with minimal disruption.
AI-powered visual inspection systems are raising the bar for quality control in manufacturing. Equipped with machine vision cameras and advanced algorithms, these systems can detect even the smallest defects with unparalleled accuracy. By ensuring the integrity of every product that leaves the factory floor, manufacturers can uphold their reputation for delivering high-quality goods to consumers.
As the manufacturing industry continues to evolve, embracing the AI revolution is essential for staying competitive in a rapidly changing landscape. By implementing AI technologies such as cobots, RPA, digital twins, predictive maintenance, and AI inspection systems, manufacturers can unlock new levels of efficiency, quality, and innovation. The future of manufacturing is AI-powered, and those who adapt will thrive in the factory of the future.
Ready to revolutionize your factory floor with AI? Explore the possibilities and transform your manufacturing processes today!
Imagine this: a critical machine fails, halting your entire production line. But what if the culprit wasn't a random breakdown, but a hacker lurking in your network?
The Internet of Things (IoT) is revolutionizing manufacturing, but with increased connectivity comes new security risks. Here's how to fortify your industrial IoT (IIoT) defenses!
Introduction
The increasing connectivity in the manufacturing sector, driven by the Internet of Things (IoT), brings along new security challenges. In this article, we'll explore five essential tips to secure your Industrial IoT (IIoT) network, ensuring the safety and efficiency of your operations.
Now, let's dive deeper into each of these crucial strategies:
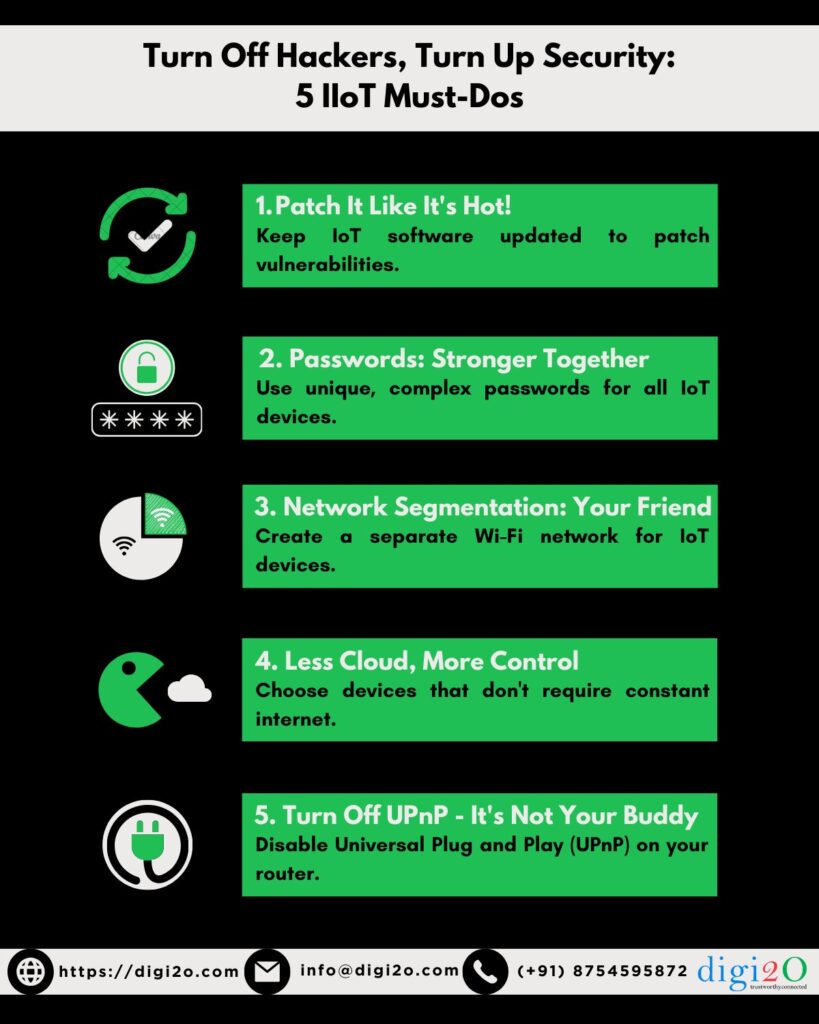
Just like your phone, IoT devices need software updates to fix vulnerabilities. Don't be complacent - install them ASAP! This might not be as automated as your PC, so stay vigilant.
Software vulnerabilities are like open doors for hackers. Just as you update your computer and phone regularly, ensure your IoT devices receive timely patches. Keep an eye on updates and apply them promptly to keep your network fortified against potential threats.
Ditch the factory default passwords! Create unique, complex passwords for every device and account. Think numbers, letters, and symbols - the more random, the better. Pro tip: Don't reuse passwords across different devices!
Default passwords are the low-hanging fruit for cyber attackers. Set strong, unique passwords for each device and account to create layers of defense. Use a combination of letters, numbers, and symbols to make them resilient against brute force attacks.
Think of your network as a fortress with multiple layers of defense. By segmenting your network and creating dedicated zones for IoT devices, you limit the impact of a breach. Even if one area is compromised, the rest of your network remains secure.
Imagine creating a separate Wi-Fi network just for your IoT devices. This way, even if a hacker breaches your IIoT network, they'll have a harder time reaching your critical systems.
While cloud services offer convenience, they also introduce vulnerabilities. Consider local solutions that reduce dependence on the cloud, minimizing the exposure of sensitive data to potential breaches. This approach puts you in control of your data and security measures.
Universal Plug and Play (UPnP) might simplify device connection, but it also creates security holes. Unless necessary, disable this feature to make life harder for potential attackers. UPnP may seem convenient, but it's a double-edged sword when it comes to security. Disabling UPnP reduces the attack surface by closing unnecessary ports and thwarting potential intruders. Take control of your network by disabling this feature unless absolutely necessary.
Conclusion
Securing your IIoT network is paramount in today's interconnected world. By implementing these five essential tips, you can bolster your defenses against cyber threats, safeguarding your operations and ensuring uninterrupted productivity.
By following these steps, you can significantly reduce your IIoT security risks. Remember, a proactive approach is essential to safeguard your factory from cyber threats!
Designed by W3Squad